Two ideas combined into a powerfull security strategy
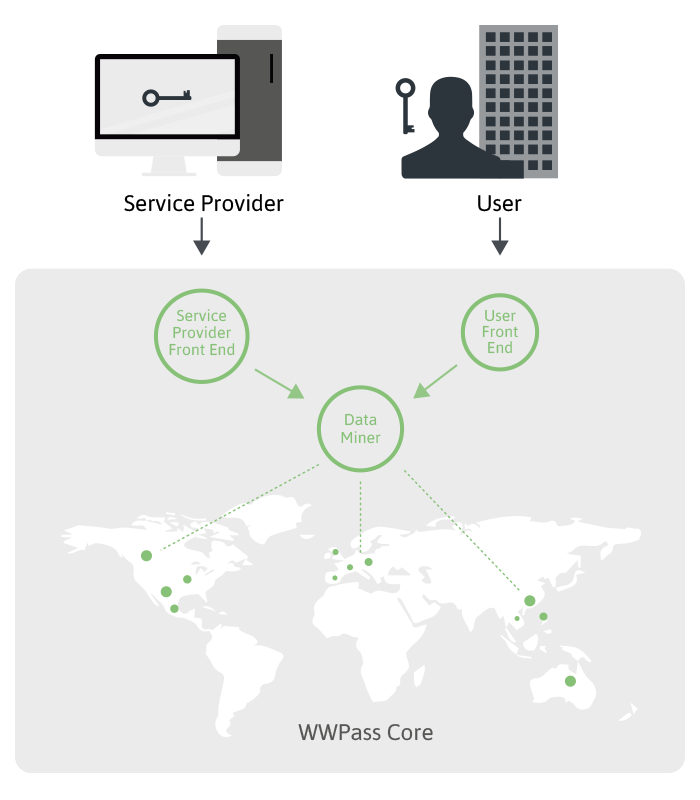
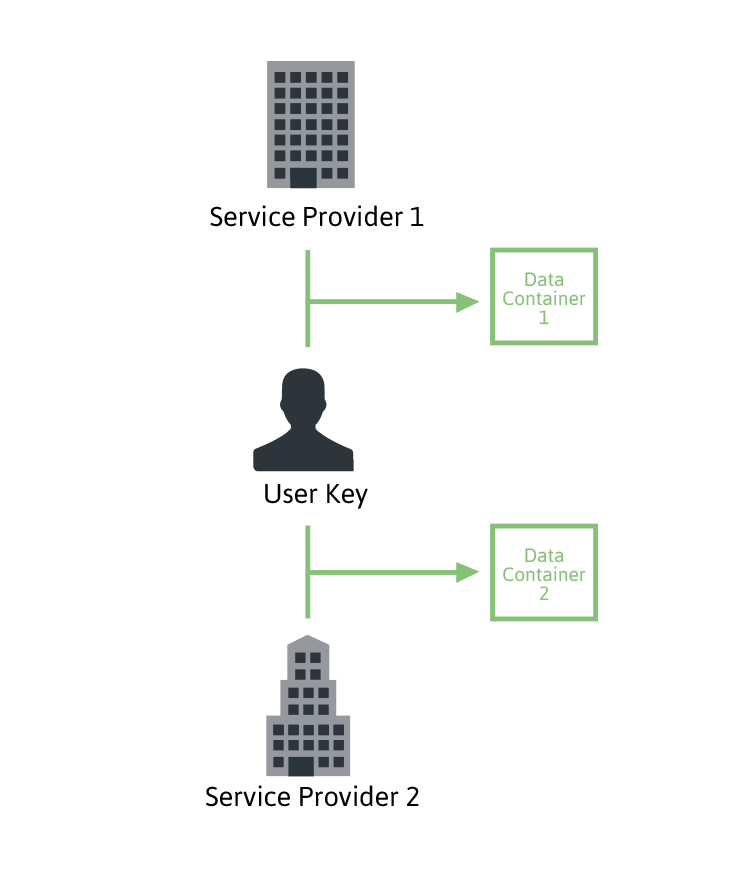
WWPass provides a unique key to every user (UserID) and another unique key for the Vendor (we call this key a SPID - Service Provider ID). The SPID is used for every vendor specific application, or public organization that must authenticate its users.
WWPass creates a separate Data Container which corresponds to each user registration at a particular Service Provider's website or application (i.e. for each UserID/SPID pair). To open this box, two keys are needed: first the user’s key (containing the UserID) and second, the Service Providers key (containing the SPID). In the reality the Data Container address is calculated as a one-way function of SPID and UserID. Another one-way function is used to cypher the Data Container content. Finally, the Data Container is dispersed over WWPass storage nodes using Reed-Solomon transformation.